Introduction
Credit Union Mergers: How Integration Chaos Can undermine Your Best Laid Plans
Credit union mergers can indeed unlock some amazing benefits: bigger economies of scale, a wider range of services to offer, and a more competitive position in the market. But make no mistake - that integration process is a minefield, where operational chaos can easily blow up and put member trust at risk, trigger regulatory heat, and essentially undo all the good you thought you were doing.
The problem isn't just about plugging in new tech - it's about being prepared for the business side of things. If you're not careful with your continuity planning, even the smallest hitches in the transition can snowball into service disruptions that seriously antagonize the very members you're trying to serve better.
What's Really at Stake: Why Integration Failures are so Damaging
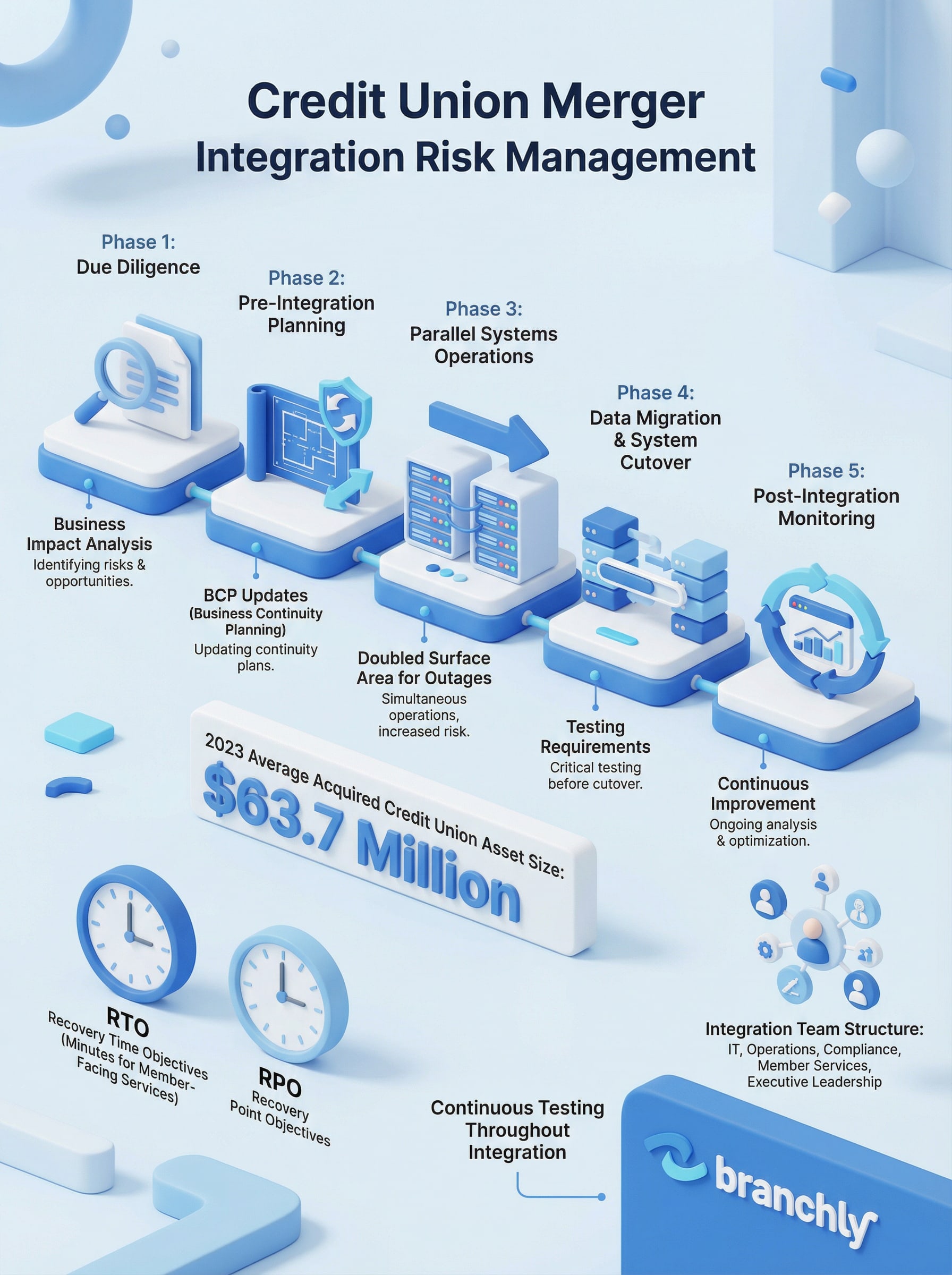
Credit union mergers have been on the rise for years now, driven by all sorts of forces: regulatory pressure, the need for tech upgrades, and the absolute necessity of getting bigger and more efficient. In 2023, the average size of a credit union getting acquired was a whoppin' $63.7 million - and that speaks to just how complex these integrations are getting.
We're not talking small-time deals here. Each credit union brings its own unique banking platform, member comms systems, compliance requirements, and operational workflows to the table - so when it comes time to integrate, you've got multiple sets of systems running side by side. And let me tell you, it's a powderkeg waiting to happen - one core system failure, a data migration glitch, or a communication breakdown can shut down member services and put the whole institution at risk of regulatory heat.
Don't even think for a second that the NCUA or FFIEC are going to give you a free pass on continuity during this time - your disaster recovery plan needs to be on point if you're running dual infrastructures. Because if it's not, you're not just risking service interruptions - you're risking a whole lot more.
Start BCP Updates Early
Don't wait until post-merger to update your business continuity plan. Begin revising your BCP during due diligence so you understand the full scope of systems, vendors, and dependencies you'll inherit.
Where Most of the Trouble Starts - The Technology Integration Conundrum
Technology integration - this is where nearly all the headaches come from in a merger - and it's no wonder why. Its a super resource-intensive and error-ridden part of the process. You're stuck dealing with clashing core platforms, overlapping contracts with vendors and trying to merge data sets that just don't naturally fit together.
Data migration problems are more common than you'd want to think and also very, very costly. Information like member account details, loan records & transaction histories need to get transferred over accurately and completely - no exceptions. And it only takes one little field mapping error to cause chaos - think about it, wrong account balances, a string of failed transactions, or the most worst of all - discrepancies in regulatory reporting.
The Parallel Systems Risk
Running dual systems during integration doubles your surface area for outages. If one system fails, members served by that platform lose access to accounts, payment processing, and support until recovery is complete.
Vendor consolidation creates its own headaches. You may be locked into overlapping agreements with redundant service providers. Terminating contracts early can trigger penalties. Keeping both vendors active longer than necessary inflates costs and complicates incident response, who do you call first when online banking goes down?
An API-first approach to integration helps manage this complexity by building modular, flexible connections between systems. It won’t eliminate risk, but it reduces the brittleness that turns small issues into full outages.
Business Impact Analysis: Your Foundation for Continuity
Before you can protect operations during a merger, you need to know what operations are critical. That’s where a Business Impact Analysis comes in. A BIA identifies which functions are essential to member service, regulatory compliance and financial stability and how long each can be down before the damage becomes unacceptable.
Your BIA should specify Recovery Time Objectives (RTOs) and Recovery Point Objectives (RPOs) for every critical system. RTO is how quickly you need to get a function back up after an outage. RPO is how much data loss you can tolerate. For member-facing services like online banking or payment processing your RTO might be measured in minutes not hours. For back office reconciliation you may have more flexibility.
During a merger your BIA needs to account for both institutions’ systems. If the acquiring credit union’s core has an RTO of 2 hours but the acquired institution’s legacy system has an RTO of 8 hours you’ve just inherited a 4x increase in exposure. You need to know that before integration day not after members start calling because they can’t get into their accounts.
Map Dependencies Across Both Institutions
Your BIA should include a full dependency map showing which systems rely on which vendors, network connections, and internal staff. Integration often breaks these dependencies in unexpected ways.
The BIA also needs to identify third-party dependencies. If the acquired credit union uses a different card processor, merchant services provider or IT support vendor, you need to know how their continuity plans intersect with yours. A vendor outage that would have been a minor inconvenience pre-merger can become a full service disruption if you haven’t coordinated backup procedures.
Testing and Drills: The Only Way to Validate Your Plan
Your business continuity plan is only as good as your ability to execute it under pressure. That means testing, not once after the merger closes, but throughout the integration process.
Tabletop exercises are the easiest place to start. Get your integration team together, walk through a scenario like a core system outage or data center failure and talk through who does what. You’ll quickly find gaps in communication protocols, unclear role assignments and missing contact information. These are low cost and low risk but they surface real problems.
Live recovery drills take it further. Actually fail over to your backup systems. Simulate a data migration rollback. Test your communication templates by sending them to a controlled group. These are disruptive and resource intensive but they’re the only way to know if your plan works in practice.
Regulators Expect Evidence
NCUA examiners want to see documentation of your testing activities, not just the existence of a plan. Maintain logs of every drill, tabletop exercise, and actual incident response with timestamps and outcomes.
After every test or incident - whether its a simulated exercise or a genuine event - Do a debrief on what went down. What worked? What didn't? Were there stages that dragged on longer than expected? Were there people unclear on their role? Pick out all the valuable lessons you learned and put them into your playbooks - so you can do better next time. Its this ongoing cycle of improvement that sets apart institutions that get back on their feet quickly from those that spend hours, days or even weeks stuck in limbo.
Communication Protocols: Keeping Everyone Informed
A merger gone wrong because an operational failure is one thing. But communication failures can make a bad situation a total disaster. If members are left in the dark - no idea what's happening, or when the service will be back up - their frustration boils over into distrust. If staff aren't clear on what they're supposed to do, they'll end up improvising - and that usually just makes things worse.
You should have pre-approved comms templates ready to go before you even start integrating. These should cover all the common scenarios: system crashes, delayed processing, branch closures, changes to service. And make sure they've been cleared by legal and compliance - so you're not stuck scrambling for approval when members are already ringing you.
Internally, communication is just as important as externally. Staff need to know what's going on, what they should tell members, and who to go to if they get stuck. During integration, people's reporting lines and responsibilities change. So make sure frontline employees have a clear point of contact for every possible problem they might hit - and that those contacts are on call when stuff starts going wrong.
Don't Overlook Vendor Communication
Your third-party service providers need to know about the merger timeline and any changes to contact information, escalation procedures, or technical configurations. A vendor can't help you recover if they don't know who to call.
When you're transparent with your members, you build trust. Say you're migrating systems over the weekend, and there's a chance of a brief outage - tell them. Give them an idea of when it might happen and what they can do if its going to be a problem. Most members will be okay with a short, planned disruption if they get advance warning. What they wont put up with is being blindsided
Regulatory Compliance: Continuity Obligations Don't Take a Break
For the NCUA and FFIEC, business continuity and operational resilience are pretty top of mind. And they dont take a back seat just because you're in the middle of a merger. In fact, regulators tend to keep a beady eye on integration periods because they know disruption is such a big risk.
So before the integration is even finished, your business continuity plan has got to be updated to reflect how things are going to look post-merger. That means documenting your new system architecture, your updated contact lists, any revised recovery procedures, and your consolidated vendor relationships. If a regulator comes in and asks to see your current BCP, and it still looks like it was written before the merger - you've got a compliance headache on your hands.
Audit trails are non-negotiable. Every single action you take during integration should be logged - who approved the data migration, when the cutover happened, what testing was done, how any issues got sorted out. If something goes wrong and regulators start asking questions, you want to be able to show you followed a sensible process.
Engage Regulators Early
Don't wait for examiners to discover integration issues. Proactively brief the NCUA on your merger timeline, continuity plans, and testing schedule. Transparency reduces regulatory risk.
Managing third-party risk gets a whole lot trickier once youve merged. You're now responsible for vendors you didnt choose and may not know much about. Just to be on the safe side, confirm that each vendor has their own BCP, that its aligned with your RTOs and RPOs, and that theyve actually put it to the test recently. If a critical vendor cant show you that theyre on top of continuity, thats a gap you need to close before you start relying on them.
Leadership and Governance: Making Continuity an Executive Priority
Business continuity planning can’t be left to IT or operations. It needs executive sponsorship and board-level oversight. Senior leadership needs to understand the operational risks in the merger and allocate resources to manage them.
Create a cross-functional integration team with clear authority and accountability. This team should include IT, operations, compliance, member services and executive leadership. They need to meet regularly, track progress against the integration plan and escalate issues before they become crises.
Succession planning matters too. Mergers result in staff turnover as roles are consolidated or eliminated. If the person who knows how to recover your core banking system leaves during integration, you’re in trouble. Document critical knowledge, cross-train staff and identify backup personnel for every key role.
Budget for Continuity Investments
Resilience costs money. Whether it's redundant systems, backup connectivity, or additional testing, make sure your integration budget includes line items for business continuity measures.
Board oversight is key. The board should receive regular updates on integration progress, including incidents, testing results and emerging risks. They need to ask tough questions: Are we confident we can maintain member service during cutover? Have we tested our recovery procedures in realistic conditions? What’s our plan if a major vendor fails?

Merger Integration Risk Framework
Key continuity checkpoints from due diligence through operational close
Continuous Improvement: Learning from Every Event
Your business continuity plan should never be static. After every drill, test or actual incident do a formal post-mortem. What did we learn? What should we change? Were our RTOs realistic? Did our communication templates work?
Document lessons learned and update your playbooks. If a recovery step took twice as long as planned, adjust your timeline. If a vendor proved unreliable, identify alternatives. If staff didn’t know how to use the backup system, schedule additional training.
Review your BCP at least annually and immediately after any significant change like a merger, new system implementation or vendor switch. Threats change. Technology changes. Your plan needs to keep pace.
Consider using dedicated business continuity software to centralize documentation, track testing activities and manage incident response. Spreadsheets and shared drives create data silos and make it hard to maintain current information across a complex, multi-location institution. Purpose-built tools give you a single source of truth and enable data-driven analysis of your continuity posture.
Summary
Mergers create real operational risks but those risks are manageable with disciplined planning, testing and executive buy in. Start with a Business Impact Analysis that covers both institutions’ systems. Build and test your business continuity plan during integration not after. Communicate transparently with members, staff and regulators. And treat continuity as an ongoing organisational responsibility not a one off compliance exercise. The institutions that get this right protect member trust, maintain regulatory standing and get the strategic benefits that made the merger attractive in the first place.
Key Things to Remember
- ✓Conduct a full Business Impact Analysis during due diligence to identify critical functions, RTOs, and RPOs across both institutions before integration begins.
- ✓Test your business continuity plan continuously throughout integration using tabletop exercises and live recovery drills to identify gaps before real incidents occur.
- ✓Prepare pre-approved communication templates for members, staff, and vendors to maintain trust and coordination during system outages or service disruptions.
- ✓Engage regulators proactively with transparent updates on your merger timeline, continuity planning, and testing results to reduce compliance risk.
- ✓Establish cross-functional integration teams with executive sponsorship and board oversight to ensure business continuity receives adequate resources and attention.
How Branchly Can Help
Branchly gives credit unions a single platform to manage operational risks throughout merger integration. Our AI-powered engine identifies critical dependencies across both institutions, generates location-specific playbooks for system outages and data migration issues, and maintains pre-approved communication templates for members, staff, and regulators. During integration, the Command Center provides real-time visibility into every branch and system, with automatic audit logging to satisfy NCUA and FFIEC requirements. After every incident or drill, Branchly's intelligence layer analyzes response times and suggests improvements, turning each event into an opportunity to strengthen your continuity posture.
Citations & References
- [1]
- [2]Merging Forward: Key Considerations for Credit Unions Planning to Consolidate — Curtis Strategy curtisstrategy.com View source ↗
- [3]Credit Unions’ Strategic Evolution: Navigating Growth Through M&A and Beyond | L.E.K. Consulting lek.com View source ↗
- [4]
- [5]
- [6]
- [7]Ensuring Business Continuity & Compliance for Credit Unions: Protecting credit union operations from disruptions cunastrategicservices.com View source ↗
- [8]
- [9]
- [10]
- [11]
- [12]Merger reasons and their impact: Evidence from the credit union industry | Journal of Economics and Finance springer.com View source ↗
